Experimenting with Telex
We have created a proof-of-concept Telex implementation to demonstrate the idea and allow other researchers to experiment with it. Our implementation consists of a Telex station running at a small “ISP” in our lab, and a Telex client program that runs on the user's computer.
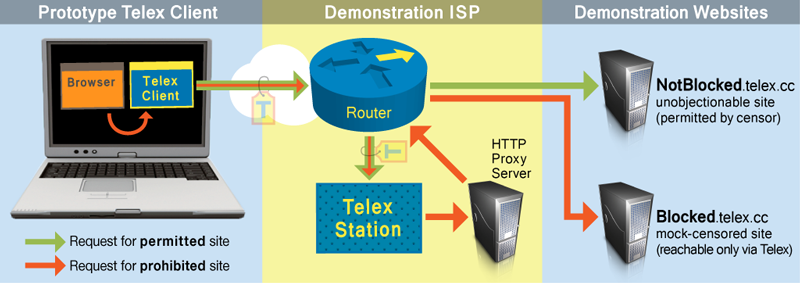
When the Telex client receives a connection from your browser, it creates an HTTPS connection to NotBlocked.telex.cc and marks the connection with our steganographic tag. The Telex station watches the connection on its way to this server. Since the station has the Telex private key, it can detect the presence of the tag and divert the connection to a proxy server.
You can experiment with Telex by downloading the Telex client software (below). The Telex client program accepts TCP connections from other software on the user's machine and tunnels them to services offered by the Telex station. For our demonstration, we have configured the Telex station to provide HTTP proxy service.
Our demonstration setup also includes two websites:
-
NotBlocked.telex.cc (a non-censored
site)
By assumption, this site is not blocked by the censor. Connections to it pass through our demonstration ISP and our Telex station. When the demonstration Telex client connects to this site, our Telex station transparently diverts the connection to a proxy server. -
Blocked.telex.cc (a censored
site)
This site simulates a server that is inaccessible due to network-based censorship. Connections to it are blocked unless they arrive through Telex.
Browsing the Web via Telex
After installing or building the Telex client, run (from a Linux command prompt):
LD_LIBRARY_PATH=./req/local/lib ./telex-client NotBlocked.telex.ccor, from a Windows command prompt:
telex-client NotBlocked.telex.ccand configure your web browser to use HTTP and HTTPS proxy servers on localhost port 8888. The browser should then be able to connect to Blocked.telex.cc.
Our proxy currently allows access to Google, Facebook, Telex.cc, Twitter, and YouTube. If your experiments require access to other sites, please contact us.
Using Tor via Telex (added 7/20/11)
Normally, the Telex station is able to see the destination of your proxied requests (e.g., the “Blocked.com” that you request via Telex). However, it is possible to use Tor, an anonymity-providing proxy, on top of Telex. This way, the Telex station will only be able to observe that you are using Tor, not your ultimate destination.
To use Telex as an entry to Tor, first make sure you've downloaded the Telex client below. You'll also need our Tor public key file, which instructs the Telex station that you want to be connected to our Tor Bridge instead of our HTTP proxy. To use this public key, run the Telex client with the additional options shown in bold:
telex-client -k tor.pubkey -p 4444 notblocked.telex.cc
Next, download the Tor Browser Bundle client (if you don't already have the most recent version), and edit your torrc file to add the following three lines:
Bridge 127.0.0.1:4444 F580401C7A5EEDD54F2927A1C161E9642D1ADCCC UpdateBridgesFromAuthority 0 UseBridges 1
At this point, launch the tor_browser_bundle, and a browser window should open using Tor over Telex. You can use this page to verify that you are connecting through Tor.
Mailing List
If you would like to be notified of future releases and Telex-related news, you can join our mailing list by sending an email to telex-users-request@umich.edu, or follow us on Twitter, @TelexBureau.
Blocking in China (added 9/17/11)
On September 16, 2011 we confirmed reports of DNS blocking in parts of China, for the notblocked.telex.cc domain. Since our current deployment only has a handful of websites that can be used as unblocked websites, this is an effective method of blocking until Telex is deployed on a wider scale.
Below is a partial list of domains that can be used to communicate with telex:
- notblocked.telex.cc
- notreallyblocked.telex.cc
- jhalderm.com
Downloads
v0.0.2 released Sep 17, 2011
Source (builds on Win32/Linux):
telex-client-0.0.2_src.tar.gz
Windows binary distribution:
telex-client-0.0.2_win32.zip


